The goal of a trust model is to minimize the number of entities that must be trusted to preserve business interests. The digital cinema trust model enables highly valued content to be distributed worldwide without encumbrance on fulfillment and exhibition entities.
The early stages of motion picture production are managed by rights owners where trust is inherent. Motion picture distribution, however, is normally conducted outside of a rights owner’s purview. Special consideration, therefore, is needed to ensure a trusted environment in distribution. The typical high level workflow model for motion pictures is illustrated below. The area of interest is that shared by Distribution and Exhibition.
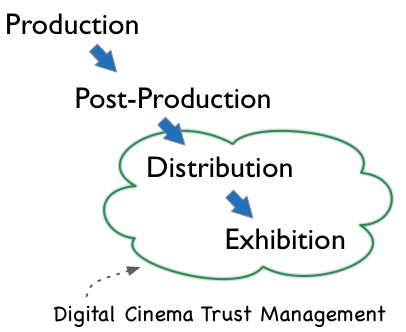
Figure TM-1. Motion Picture Workflow
Trust is ensured through the encryption of digital cinema content and the management of security keys that enable the content to be played. For practical reasons, it’s useful to encrypt once and distribute to many, in a one-to-many fashion. But it’s also desirable to restrict where encrypted content is played, enabling playout in a site-by-site or screen-by-screen manner per the business requirements of the rights owner.
Cinema is unique in the digital media world in that it’s relatively small footprint of approximately 150,000 screens worldwide allows it to be managed as a closed ecosystem. Content encryption is managed such that the matter of trust is further narrowed, away from exhibitors, and towards an even smaller number of actors: the equipment manufacturers.
The security specification to which equipment must comply is jointly owned and managed by the six major Hollywood studios, whose content generates a substantial share of box office for cinemas. The joint specification is published by Digital Cinema Initiatives (DCI), a consortium of the six major studios. DCI maintains a website for its Digital Cinema System Specification (DCSS) and Compliance Test Plan (CTP) at dcimovies.com.
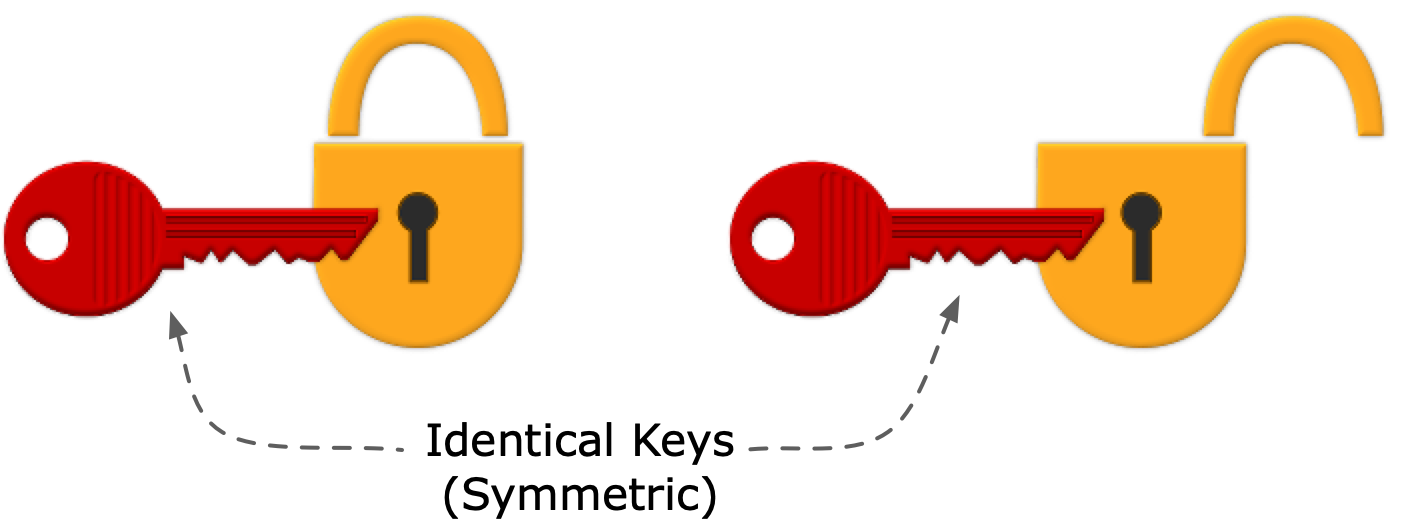
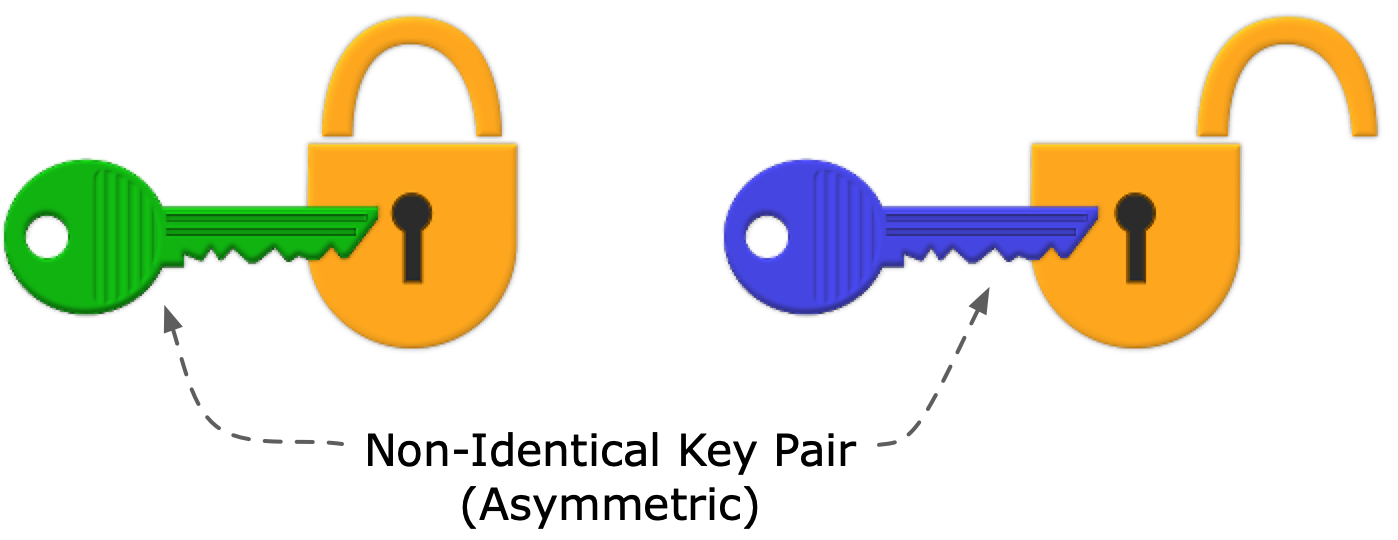
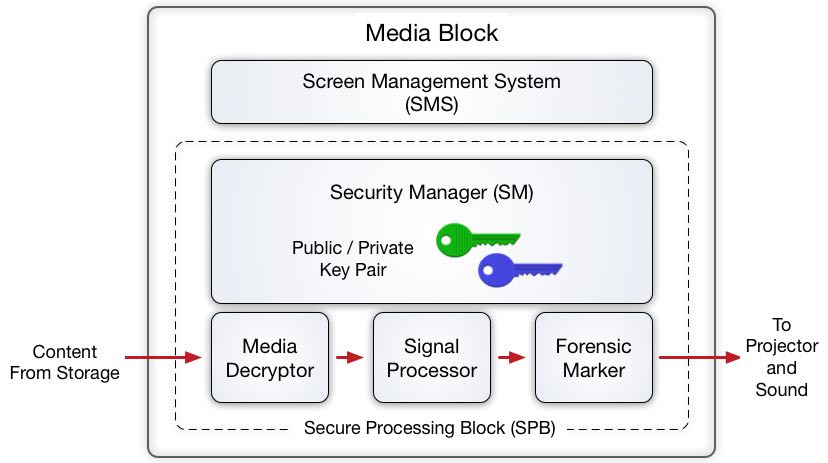
Digital cinema security utilizes a combination of symmetric key encryption and private key infrastructure, incorporating the principles of openness and autonomy. Openness ensures that the system can be built by anyone skilled in the art, based on royalty-free and license-free standards and specifications. Autonomy means that securely distributed content can be played without the need for active connection of the playback equipment to an outside network.
The principle of autonomy requires that the playback equipment manage its own trustworthiness. For this reason, DCI-compliant equipment is tamperproof by design, eliminating the need for active verification. Each certified playback device has at least one Digital Cinema Certificate, recognized by DCI as a declaration the device meets the DCI Specification.
The digital cinema trust model allows for closure of this open loop of trust by means of the Digital Cinema Security Log. The log establishes a “Circle of Trust” workflow model, as illustrated below.
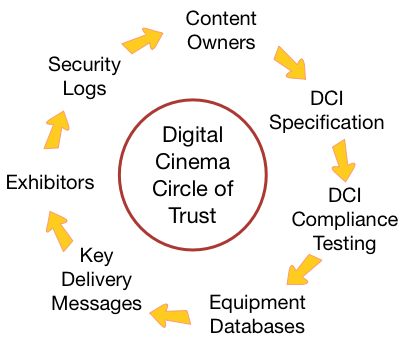
Figure TM-2. The DCI Model of Control Lightly/Audit Tightly
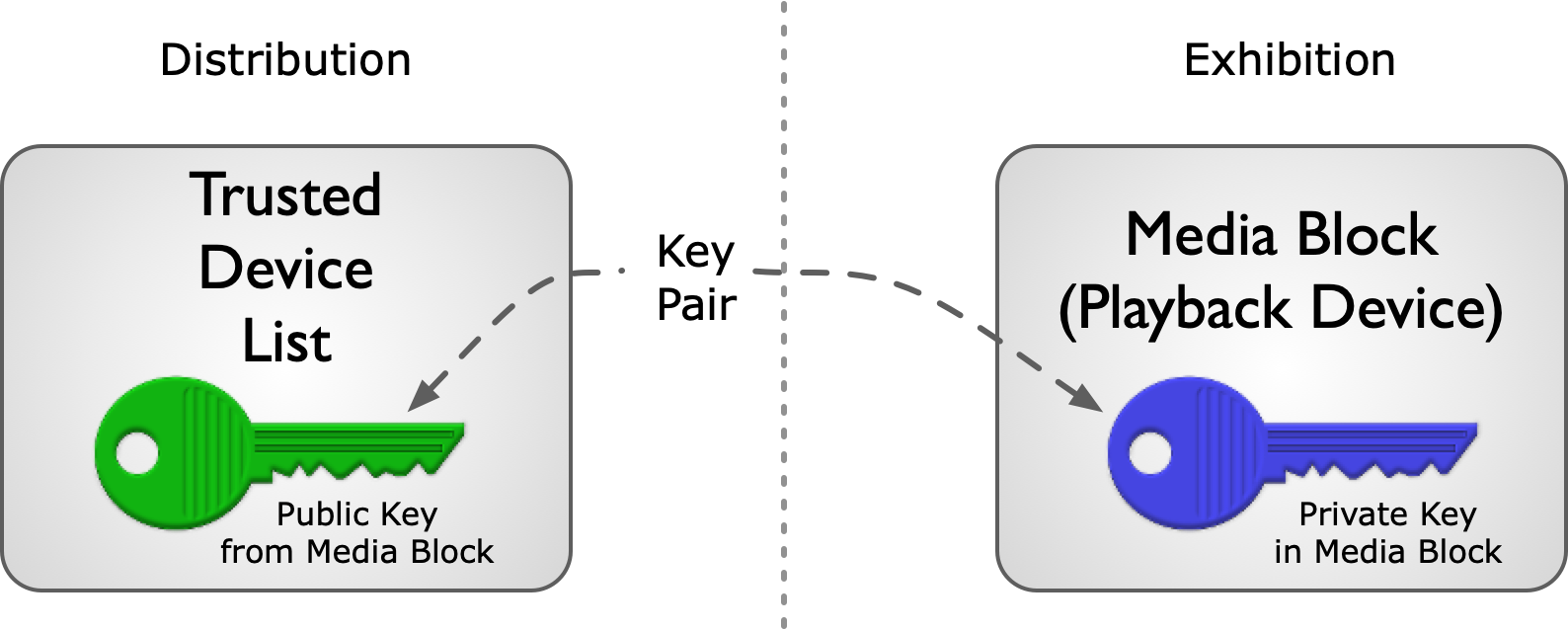
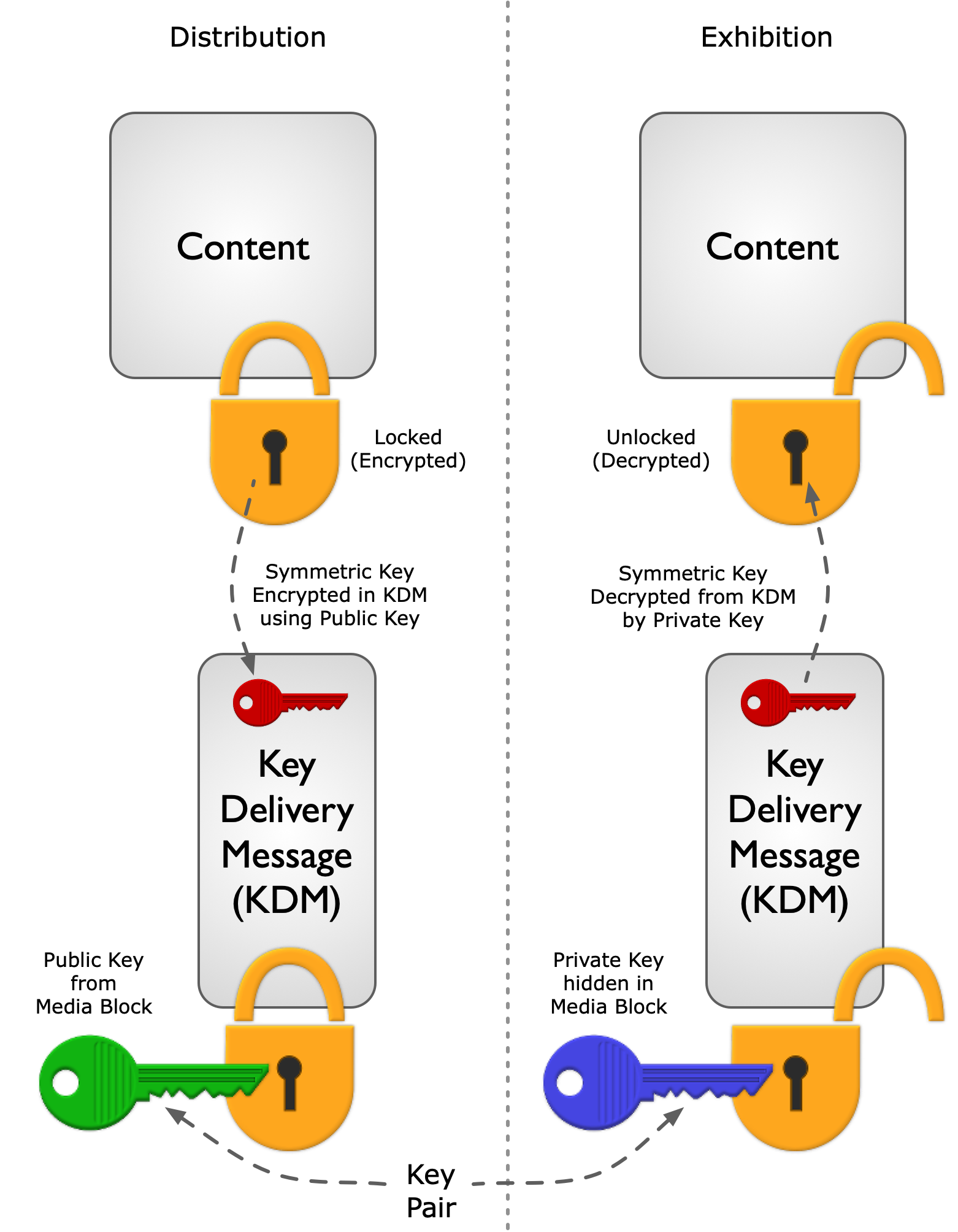
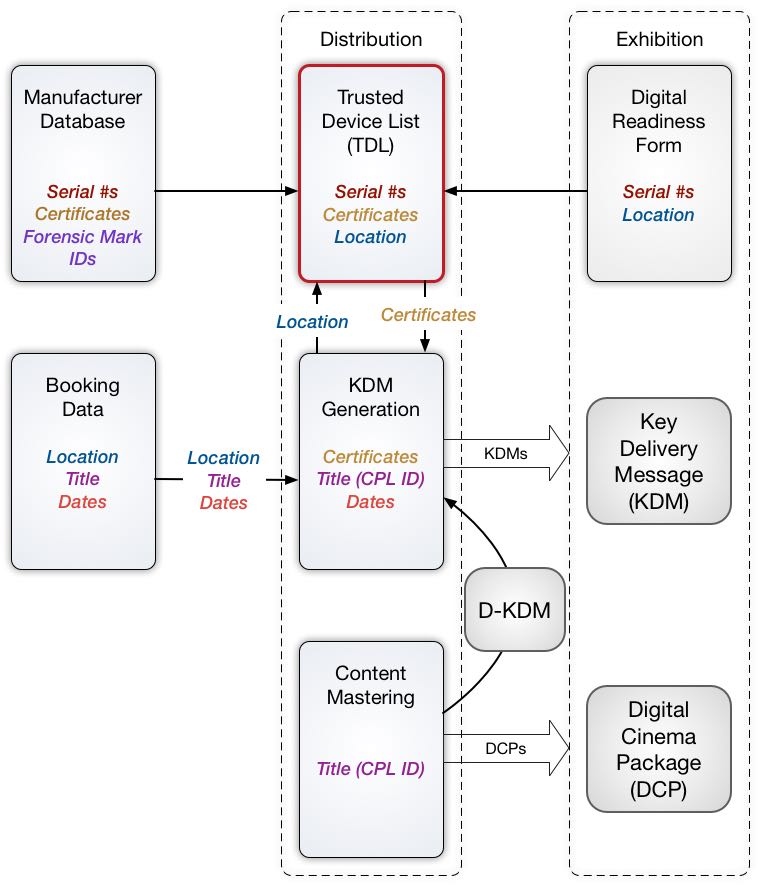
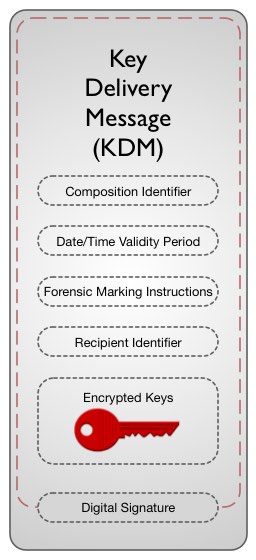
Content owners publish the DCI Specification, which is the basis for DCI Compliance Testing of digital cinema equipment. Certified devices carry a digital public-key certificate, whose serial number and public key are recorded in a database commonly referred to as a “Trusted Device List,” or TDL. The TDL also records where the certified device has been installed. When content is encrypted, the encryption key is distributed in encrypted form as a Key Delivery Message, or KDM. The exhibitor receives both the encrypted content and the KDM, enabling the content to play. At the time of playout, a Security Log is generated by the DCI-compliant playback system, which can then be viewed by the content owner to validate that its content was played by DCI-compliant equipment. The DCI specification refers to this closed loop process of managing trust as “control lightly/audit tightly.” (See DCI, DCSS section 9.4.6.3 Logging System.)
In practice, it is often sufficient for rights owners to trust the public keys made available to them by equipment manufacturers. For an exhibitor to receive the proper keys that enables content to play, it must report the equipment in its possession, completing the TDL.
To summarize, the digital cinema trust model is managed within an ecosystem that does not require active verification of playback equipment. Equipment manufacturers establish trust in their equipment through the certification process established by DCI. Content owners express trust in an exhibitor’s playback equipment when creating Key Delivery Messages (KDMs) based on Trusted Device Lists (TDLs). In addition, content owners can close the trust loop through the examination of equipment Security Logs.