
KDM is the acronym for Key Delivery Message. A KDM is required to play an encrypted movie. Each KDM enables one version of the movie to play on a target playback device for a limited duration, which could be hours, weeks, or months.
The KDM is the vehicle for securely delivering symmetric content encryption keys to authorized playback equipment. A KDM targets only one playback device, and is an expression of trust in the targeted device. Further, the trust conveyed by a KDM is only expressed for one encrypted Composition. Content versions, expressed as a separate Composition, require a different KDM to play it.
Symmetric keys carried by the KDM are encrypted, making the KDM intrinsically secure. It does not rely on a secure transport, such as TLS, to secure the keys it carries. For example, a KDM can be posted on a public web page, with the only possible outcome being that the single device authorized by the KDM will be capable of playing the associated content in accordance with the conditions carried in the KDM.
It follows that trust is expressed at the time of creation of the KDM, and not in the distribution of the KDM. This reduces the distribution of the KDM to a matter of pure logistics, without concern for the security of the transport mechanism. If a KDM arrives at the wrong destination, for example, the security of the Composition it addresses will not be compromised.
In performing its role as the communicator of trust, the KDM carries certain data:
- Encrypted symmetric content keys necessary to play an encrypted Composition
- Composition identifier associating the KDM with the Composition for which it was created
- Date/time validity period for use of the content keys
- Forensic marking instructions
- Identifier of the targeted media block (the “recipient”)
KDM Payload
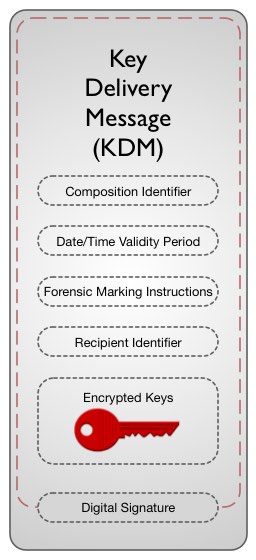
Key Delivery Message (KDM) Payload
Composition Identifier. The Composition Identifier is that carried by the associated Composition Playlist, in the form of a Universally Unique Identifier (UUID), per RFC 4122.
Date/Time Validity Period. The Date/Time Validity Period is carried in multiple ways. The information is described in clear-text (unencrypted) XML parameters as “not valid before” and “not valid after” UTC date-times, enabling the receiving equipment to readily read it. However, the actual UTC date-times to which playback equipment respond are encrypted along with each symmetric content key, where the information cannot be tampered with. The Validity Period clear-text date-time values of a valid KDM must match the encrypted date-time values.
Forensic Marking Instructions. By default, encrypted picture and sound content will be forensically marked in real-time when played by a DCI-compliant media block. A flag may be set in the KDM to command the playback system to not forensically mark the content, or to selectively mark the content. Possible reasons for taking such action include honoring a director’s wish to not modify in any manner picture or sound for a premier. A more common reason for exercising this flag is to selectively mark audio channels so that associated non-audio information carried in the audio track file, such as motion seat data, is not modified by the forensic marking engine.
Recipient Identifier. A KDM identifies the recipient (its target media block) by carrying the thumbprint (hash) of the public key of the media block’s Digital Cinema Certificate. In DCI-compliant equipment, the certificate meets the requirements of SMPTE ST 430-2 Digital Cinema Certificate, which constrains the widely used X.509v3 certificate for digital cinema applications. ST 430-2 dictates that the dnQualifier attribute of the certificate’s Subject Name contain the public key thumbprint of the recipient, serving as an identifier. This thumbprint is also carried in the KDM, as the KDM must carry the Subject Name of the certificate.
The thumbprint is a computed hash, using the SHA-1 hashing algorithm, of the media block’s public key. The computed hash is computationally unique, irreversible, and repeatable. It is unique in that a change of a single bit in the public key will cause a change in the hash value. It is irreversible in that one cannot reconstruct the public key from the thumbprint. In practice, a Theater Management System can use the thumbprint to efficiently push KDMs to the right target devices. Alternatively, a media block can use the thumbprint to identify and pull KDMs intended for it from a large collection of KDMs.
Encrypted Keys. The primary payloads of the KDM are the encrypted symmetric keys used to secure the associated Composition. Each Composition is comprised of at least two track files: a picture track file and a sound track file. Each track file may be divided into multiple files of essence along temporal boundaries. Each essence file that results must be encrypted with a unique symmetric key. From this, it should be apparent that a large number of symmetric content keys could be employed with a long Composition. Each content key is encrypted with the public key of the recipient (the target media block), and included in the KDM. The KDM specification requires that the key identifier and validity dates be encrypted along with each key. The key identifier is defined in SMPTE ST429-6 MXF Track File Essence Encryption, and is used by the media block to match each key with its associated track file.
Digital Signature. The KDM is digitally signed following the XML signature specification of W3C. Details of the signature are described in SMPTE ST430-3 Extra-Theater Message and SMPTE 430-2 Digital Cinema Certificate.
D-KDM and KDM Standards
In practice, when a Composition is encrypted, the encrypting device simultaneously creates a KDM for secure storage of the symmetric content keys used during the encryption process. This KDM, and similar KDMs created for use in pre-distribution applications, are called Distribution KDMs, or D-KDMs. For example, the Composition may be encrypted by a studio, and then sent to a fulfillment entity for re-distribution to exhibitors. At the time of encryption, the studio will also create a D-KDM targeted to a trusted device owned by the fulfillment entity. The fulfillment entity will then use the D-KDM to create exhibition KDMs for distribution, using the symmetric keys carried by the D-KDM, along with the associated booking information and playback equipment public keys found in the fulfillment entity’s Trusted Device List. It’s important to note that a D-KDM and an exhibition KDM are identical in structure, and only different in name and application.
Structurally, the KDM is a form of a generic message type called Extra-Theater Message (ETM). The designers of the ETM envisioned a class of security messages that would require the common set of features defined by this message type. However, in practice, only the KDM utilizes the ETM. For this reason, two SMPTE standards, SMPTE ST430-1 KDM and SMPTE ST430-3 ETM, are required for a complete definition of the KDM.